Device registration is performed by the user after previous authentication.
1. High Level Flow
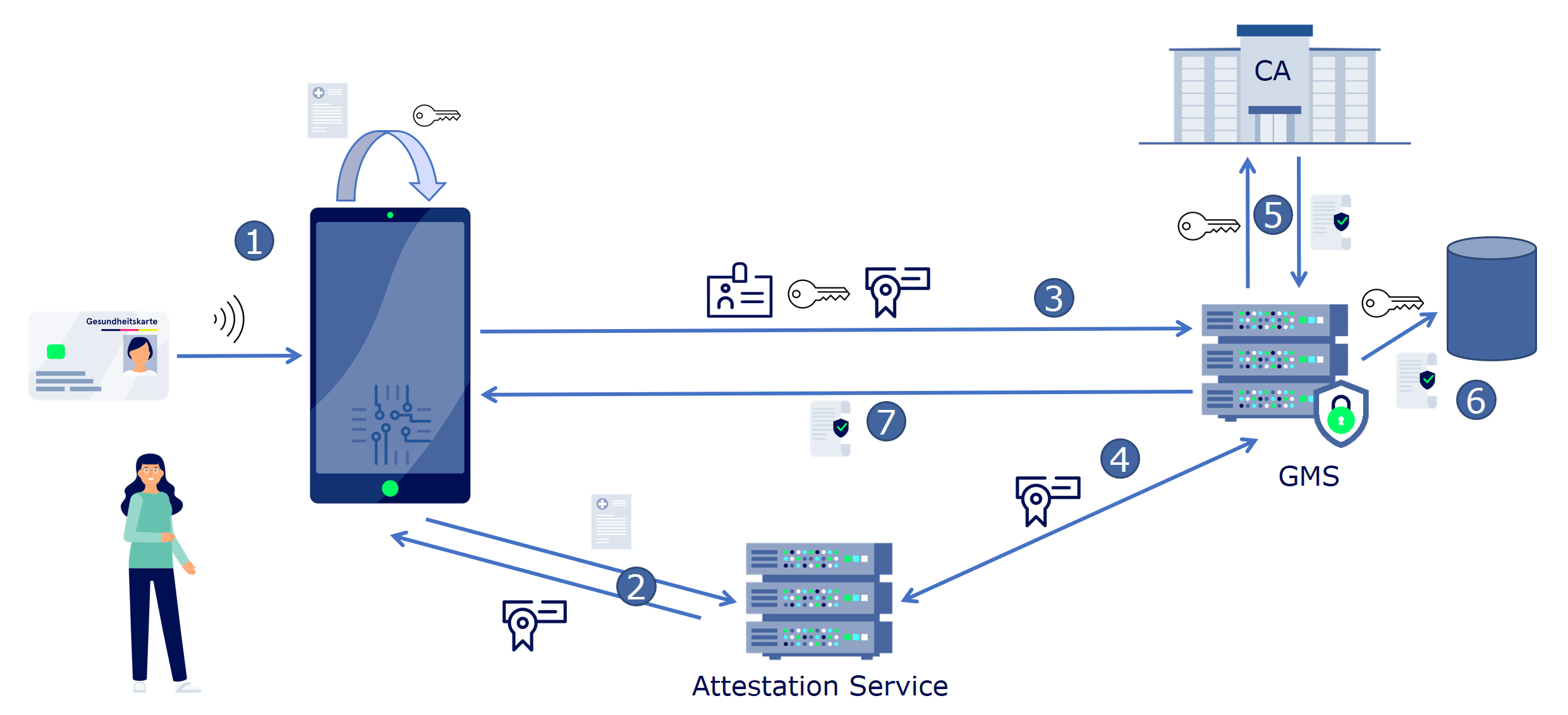
- At first start, the
TrustClientgenerates the app/device identity key material and a correspondingCertificate Signing Request. - The
TrustClientthen triggers the attestation of the key material, device and app with the help of thePlatform Attestation Serviceand receives attestation results. - To register the device for themself, the user signs a Device Registration Token, containing the app/device identity and attestation results and the
Certificate Signing Requestwith their electronic health card (EF.C.CH.AUT.E256). Then theTrustClientsends the Device Registration Token to theDevice Management Service (GMS). - With the help of the
Platform Attestation Service, theDevice Management Service (GMS)verifies the received attestations and key material. - The
Device Management Service (GMS)sends theCertificate Signing Requestto theGMS CAwhich then issues aTrust Client Certificate - Finally, the
Device Management Service (GMS)stores the app/device identity key material with the corresponding user identity in its database. - The
Device Management Service (GMS)sents theTrust Client Certificateto theTrustClient.
2. Flow Details
@startuml DSR-RFC-01 Main Flow
autonumber "<b>[00]"
skinparam defaultFontSize 10
skinparam defaultFontName Helvetica
skinparam DefaultMonospacedFontName Courier
skinparam lengthAdjust none
participant TrustClient
participant Smartcard
participant GMS
activate TrustClient
TrustClient -> GMS ++: get ""nonce""
note right
Regular TLS
Server auth only
end note
GMS -> GMS: generate ""nonce""\n store ""nonce""
GMS -> TrustClient: return ""nonce""
TrustClient -> TrustClient: derive nonces\n\t""nonce_keypair_mTLS = SHA256(nonce | 'KEYPAIR_MTLS')""\n\t""nonce_CSR_mTLS = SHA256(nonce | 'CSR_MTLS')""\n\t""nonce_Integrity = SHA256(nonce | 'INTEGRITY')""\n\t""nonce_smartcard = SHA256(nonce | 'SMARTCARD')""\n\t""nonce_attest = SHA256(nonce | 'ATTEST')""
alt#FEFFD5 2.1.1 Create Android Device Registration
TrustClient -> TrustClient: generate key pair and\ncreate ""JWT_registration""
else 2.2.1 Create Apple Device Registration
TrustClient -> TrustClient: generate key pair and\ncreate ""JWT_registration""
end
TrustClient -> Smartcard ++: sign ""(JWT_registration, nonce_smartcard)""\n\twith ""PrK.CH.AUT.E256""/""EF.C.CH.AUT.E256""
return return JWS_registration_signed
TrustClient -> GMS: register device JWS(JWS_registration_signed)
GMS -> GMS: verify JWS_registration_signed
GMS -> GMS: check EF.C.CH.AUT.E256 validity
note left
gematik PKI OCSP
end note
alt#FEFFD5 2.1.2 Verify Android Device Registration
GMS -> GMS: verify ""JWS_registration_signed""\nextract Android specifics
else 2.2.2 Verify Apple Device Registration
GMS -> GMS: verify ""JWS_registration_signed""\nextract Apple specifics
end
GMS -> GMS: extract KVNR from EF.C.CH.AUT.E256\nin JWS_registration_signed
GMS -> GMS: create cert_mTLS(CSR, UUID_device, nonce)
alt#FEFFD5 Store Android Device Registration
GMS -> GMS: store\n\tKVNR\n\tUUID_device\n\tcert_mTLS\n\tcert_attest
else Store Apple Device Registration
GMS -> GMS: store\n\tKVNR\n\tUUID_device\n\tcert_mTLS\n\tattestation_statement
end
return return cert_mTLS
TrustClient -> TrustClient: store cert_mTLS
@enduml
2.1 Android specifics
2.1.1 Create Android Device Registration
@startuml
autonumber "<b>['2.1.1' 00]"
skinparam defaultFontSize 10
skinparam DefaultMonospacedFontName Courier
skinparam lengthAdjust none
activate TrustClient
participant PlayIntegrityAPI
group Android
TrustClient -> TrustClient: generate\n\t""keypair_attest""\n\t""attestCertChain(nonce_attest)""\n\t""keypair_mTLS""\n\t""keypair_mTLS_cert(nonce_keypair_mTLS)""\n\t""CSR(nonce_CSR_mTLS, keypair_mTLS)""
TrustClient -> PlayIntegrityAPI ++: perform IntegrityTokenRequest(nonce_Integrity)
return return integrityVerdict
TrustClient -> TrustClient: create\n\t""JWT_registration(""\n\t\t""TYPE_ANDROID,""\n\t\t""nonce,""\n\t\t""pubkey_mTLS,""\n\t\t""keypair_mTLS_cert,""\n\t\t""pubkey_attest,""\n\t\t""attestCertChain""\n\t\t""integrityVerdict,""\n\t\t""CSR""\n\t"")""
end
@enduml
2.1.2 Verify Android Device Registration
@startuml
autonumber "<b>['2.1.1' 00]"
skinparam defaultFontSize 10
skinparam DefaultMonospacedFontName Courier
skinparam lengthAdjust none
activate GMS
participant GoogleServer
group Android
GMS -> GMS: extract nonce, pubkey_mTLS, AttestCert_mTLS,\nintegrityVerdict, CSR from JWS_registration_signed
GMS -> GMS: verify attestCertChain and certification extension data
GMS -> GMS: verify AttestCert_mTLS and certification extension data
GMS -> GMS: verify AttestCert_mTLS was signed by pubkey_attest
GMS -> GoogleServer ++: get Key Attestation certificate revocation status list
return return CRL_json
GMS -> GMS: evaluate CRL_json
GMS -> GoogleServer ++: request integrity_verdict(integrityVerdict)
return return verdict_json
GMS -> GMS: evaluate verdict_json
end
@enduml
2.2 Apple specifics
2.2.1 Create Apple Device Registration
@startuml
autonumber "<b>['2.2.1' 00]"
skinparam defaultFontSize 10
skinparam DefaultMonospacedFontName Courier
skinparam lengthAdjust none
activate TrustClient
participant AppAttestAPI
group Apple
TrustClient -> TrustClient: generate\n\t""keypair_mTLS""\n\t""CSR(nonce_CSR_mTLS, keypair_mTLS)""
TrustClient -> AppAttestAPI ++: generate\n\t""keypair_attest(""\n\t\t""SHA256(nonce_Integrity | SHA256(pubkey_mTLS))""\n\t"")""
AppAttestAPI -> AppAttestAPI: attest
return return attestation_statement
TrustClient -> TrustClient: create\n\t""JWT_registration(""\n\t\t""TYPE_IOS,"",\n\t\t""nonce,""\n\t\t""pubkey_mTLS,""\n\t\t""attestation_statement,""\n\t\t""keyIdentifier_attest,""\n\t\t""CSR""\n\t"")""
end
@enduml
2.2.2 Verify Apple Device Registration
@startuml
autonumber "<b>['2.2.2' 00]"
skinparam defaultFontSize 10
skinparam DefaultMonospacedFontName Courier
skinparam lengthAdjust none
activate GMS
group Apple
GMS -> GMS: extract nonce, pubkey_mTLS, attestation_statement,\nkeyIdentifier_attest, CSR
GMS -> GMS: verify attestation_statement
end
@enduml