Introduction
This RFC defines which Zero Trust signals are collected on- and off-device for security rating.
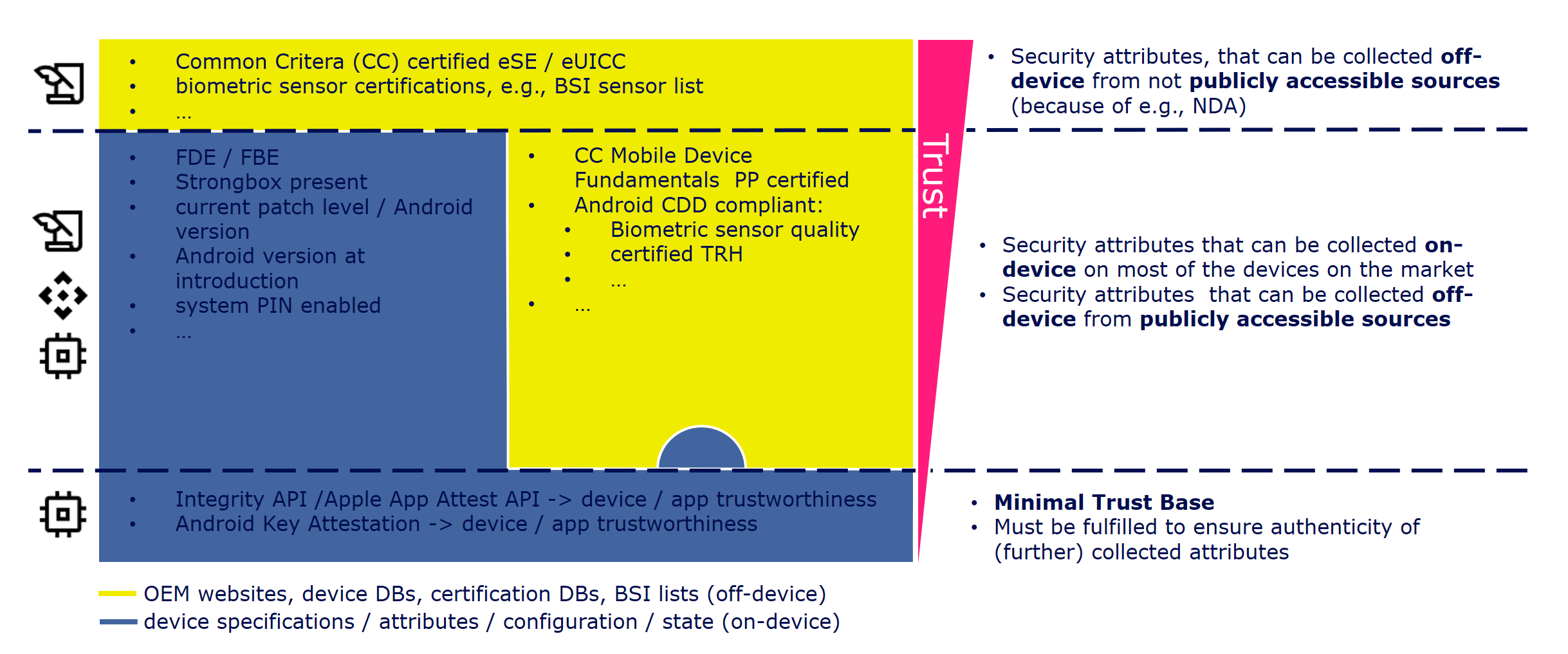
Minimal Trust Base for Registration
Minimal/basic trust that is needed for a successful registration at GMS and thus for participating in the DSR. Is verified by GMS during registration process.
Android
Google Play Integrity API
Descriptions are partially taken from the Android Developers Play Integrity doucmentation.
| Attribute | Expected Value | Description | |
|---|---|---|---|
| requestDetails: | |||
| requestPackageName | is equal to packageName from token payload and from AppIntegrity | application package name the attestation was requested for check list with enrolled apps at GMS | |
| nonce | nonce_Integrity | base64-encoded URL-safe no-wrap nonce provided by the developer | |
| timestampMillis | t + 10 min < time of creation on device | timestamp in milliseconds when the request was made | |
| appIntegrity: | |||
| appRecognitionVerdict | PLAY_RECOGNIZED | app and certificate match the versions distributed by Google Play | |
| packageName | must be in the list of available packages | package name of the app check list with enrolled apps at GMS | |
| certificateSha256Digest | must be equal to the sha256 digest, defined in the available packages list | sha256 digest of app certificates check list with enrolled apps at GMS | |
| versionCode | must be in the list of available packages | version of the app check list with enrolled apps at GMS | |
| deviceIntegrity: | |||
| deviceIntegrity | MEETS_DEVICE_INTEGRITY | app is running on an Android device powered by Google Play services, device passes system integrity checks and meets Android compatibility requirements | |
| accountDetails: | |||
| appLicensingVerdict | LICENSED | user has an app entitlement (user installed or bought your app on Google Play) | |
Android Key & ID Attestation
Descriptions are partially taken from the Android Developers Key & ID Attestation article.
| Attribute | Expected Value | Description |
|---|---|---|
| KeyDescription: | ||
| attestationVersion | tbd | version of the key attestation feature. |
| attestationSecurityLevel | TrustedEnvironment (1), StrongBox (2) | security level of the attestation |
| keyMintVersion / keymasterVersion | tbd | security level of the attestation |
| keyMintSecurityLevel / keymasterSecurityLevel | tbd | security level of the Keymaster/KeyMint implementation |
| attestationChallenge | nonce_keypair_attest | challenge from creation |
| softwareEnforced | out of scope for PoC | |
| teeEnforced | out of scope for PoC | |
iOS
App Attest Service
Descriptions are partially taken from the Apple Developer DeviceCheck documentation.
| Attribute | Expected Value | Description | |
|---|---|---|---|
| Attestation: | |||
| RP ID (32 bytes) | must be equal to the RP ID, defined in the available packages list at GMS | A hash of your app’s App ID, which is the concatenation of your 10-digit team identifier, a period, and your app’s CFBundleIdentifier value | |
| counter (4 bytes) | ignored for PoC | value that reports the number of times your app has used the attested key to sign an assertion | |
| aaguid (16 bytes) | production | App Attest–specific constant that indicates whether the attested key belongs to the development or production environment | |
| credentialId (32 bytes) | must be equal to the key used to sign the mTLS public key | hash of the public key part of the attested cryptographic key pair | |
Device Rating Attributes
Device security attributes that need to be provided by a device when trying to access a resource. GMS verifies token authenticity / integrity as well as app/Trust SDK info and forwards all information in device_token to PEP.
Android
Google Play Integrity API
see Minimal Trust Base for Registration.
Android Key & ID Attestation
see Minimal Trust Base for Registration.
Additional Security Attributes
Descriptions are partially taken from the Android Enterprise Developers Zero Trust signals documentation.
| Attribute | Description | API | Root of Trust | Availability |
|---|---|---|---|---|
| Android version | Android version or API level / SDK version currently running on the device | Build.VERSION.SDK_INT | Software | >= Android 1.6 |
| Android version (release) | Android version (API level) with which the device was released / CTS was passed | getprop('ro.product.first_api_level') | Software | TODO |
| Patchlevel | OS patch level | Build.VERSION.SECURITY_PATCH | Software | >= Android 6.0 |
| FDE / FBE | Indicates whether device encryption is supported and whether it is activated. | getprop('ro.crypto.state') | Software | TODO |
| System PIN / password / pattern set | Indicates whether a PIN/pattern/password is set for the lock screen. | KeyguardManager.isDeviceSecure(), BiometricManager.canAuthenticate(BiometricManager.Authenticators.DEVICE_CREDENTIAL), BiometricManager.canAuthenticate(BiometricManager.Authenticators.BIOMETRIC_STRONG) | Software | >= Android 6.0, >= Android 11, >= Android 12 |
| System PIN / password / pattern quality | The Device Policy Manager can be used to query whether certain password complexity levels are currently being met. | DevicePolicyManager.getPasswordComplexity(), requires android.permission.REQUEST_PASSWORD_COMPLEXITY | Software | >= Android 10 |
| Verified boot supported | Indicates whether VerifiedBoot is available on the device. | PackageManager.FEATURE_VERIFIED_BOOT | Software | >= Android 5.0 |
| Mainline patch level | Indicates when the last mainline patch was installed. | PackageManager.getPackageInfo("com.google.android.modulemetadata", 0).versionName | Software | API level > 1 |
| OEM / model | Returns information about manufacturer, model, etc. | BUILD.MODEL, BUILD.PRODUCT, BUILD.MANUFACTURER, BUILD.BOARD | Software | |
| Biometric class | Returns information if class 3 biometrics is available. | BiometricManager.canAuthenticate(Authenticators#BIOMETRIC_STRONG) | Software | >= Android 12 |
iOS
App Attest Service
Descriptions are partially taken from the Apple Developer DeviceCheck documentation.
| Attribute | Expected Value | Description | |
|---|---|---|---|
| Assertion: | |||
| RP ID (32 bytes) | must be equal to the RP ID, defined in the available packages list at GMS | A hash of your app’s App ID, which is the concatenation of your 10-digit team identifier, a period, and your app’s CFBundleIdentifier value | |
| counter (4 bytes) | ignored for PoC | value that reports the number of times your app has used the attested key to sign an assertion | Fraud Risk (optional): | tbd |
Additional Security Attributes
| Attribute | Description | API | Root of Trust | Availability | |
|---|---|---|---|---|---|
| System Name | The name of the operating system running on the device. | UIDevice: var systemName: String { get } | Software | >= iOS 2.0 | |
| System version | The current version of the operating system. | UIDevice: var systemVersion: String { get } | Software | >= iOS 2.0 | |
| Model | Possible examples of model strings are ”iPhone” and ”iPod touch”. | UIDevice: var model: String { get } | Software | >= iOS 2.0 | |
| identifierForVendor | An alphanumeric string that uniquely identifies a device to the app’s vendor. | UIDevice: var identifierForVendor: UUID? { get } | Software | >=iOS 6.0 | |
| App Version | The current version of the App system. | tbd | Software | tbd |