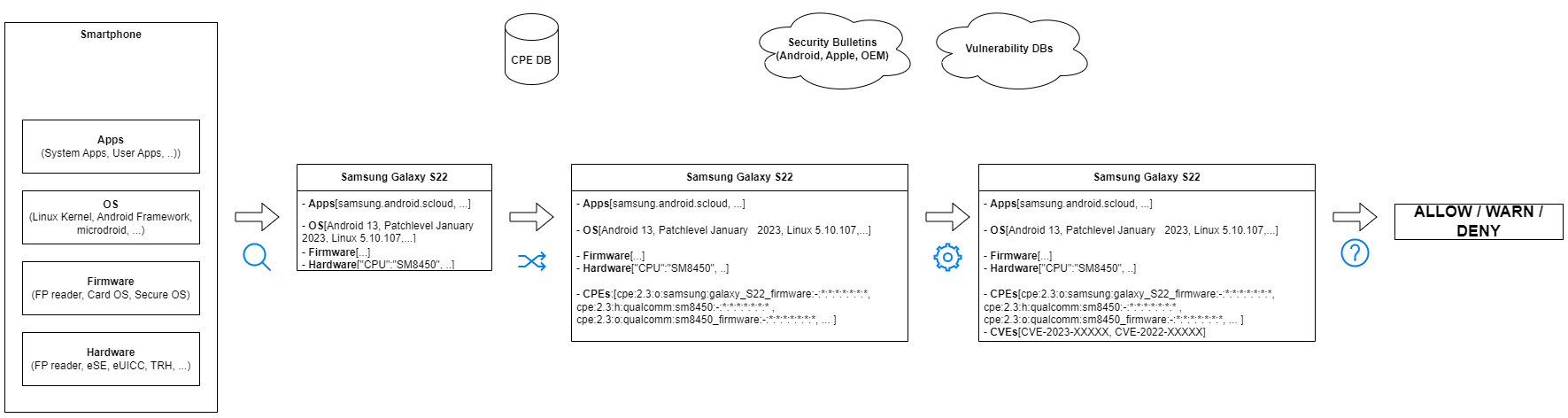
Introduction
tbd
Example Vulnerabilities
Mali GPU Kernel Driver may elevate CPU RO pages to writable
| Title | Mali GPU Kernel Driver may elevate CPU RO pages to writable |
| CVEs |
|
| Published | Spring 2022 Summer 2022 |
| Severity | MEDIUM HIGH |
| Description | A non-privileged user can get a write access to read-only memory pages; by forcing the kernel to reuse these pages as page tables, an attacker with native code execution in an app context could gain full access to the system, bypassing Android’s permissions model and allowing broad access to user data. |
| Affected Devices | Devices with Mali GPU:
|
| Needed Information to detect |
|
| CPE (via NVD) | nn |
| ✅ Rule(s) for DSR | WARN all devices with MALI GPU && tbd Patchlevel |
| References | https://googleprojectzero.blogspot.com/2022/11/mind-the-gap.html |
Samsung TrustZone Keymaster
| Title | Samsung TrustZone Keymaster |
| CVEs |
|
| Published | Spring 2022 |
| Severity | HIGH |
| Description | KeyMaster in TEE:
|
| Affected Devices |
|
| CPE (via NVD) |
|
| ✅ Rule(s) for DSR |
|
| Needed Information to detect |
|
| References |
Internet to Baseband Remote Code Execution Vulnerabilities in Exynos Modems
| Title | Internet to Baseband Remote Code Execution Vulnerabilities in Exynos Modems |
| CVEs |
|
| Published | Spring 2022 |
| Severity | HIGH |
| Description | KeyMaster in TEE:
|
| Affected Devices | Devices with Exynos 1280, 2200, 5300 modem (CVE-2023-28613):
|
| Needed Information to detect | Devices with Exynos 1280, 2200, 5300 modem (CVE-2023-28613):
|
| CPE (via NVD) |
|
| ✅ Rule(s) for DSR | 1.-4.: allow an attacker to remotely compromise a phone at the baseband level with no user interaction, and require only that the attacker know the victim’s phone number 5.-??.: require either a malicious mobile network operator or an attacker with local access to the device |
| References |
Smartphone Fingerprint Authentication Brute-force Attack
| Title | Smartphone Fingerprint Authentication Brute-force Attack |
| CVEs | nn |
| Published | Spring 2023 |
| Severity | HIGH |
| Description | Smartphone Fingerprint Authentication to Brute-force Attack with physical access |
| Affected Devices |
|
| Needed Information to detect |
|
| CPE (via NVD) | nn |
| ✅ Rule(s) for DSR | tbd |
| References | https://arxiv.org/pdf/2305.10791.pdf |
Implementation
The implementation of the pipeline was carried out using the following resources:
The main.py file receives a list of “keywords” such as “python3 main.py samsung galaxy s6”. These keywords are searched for in a local redis-server instance, which contains all CPEs from NIST.
The found CPEs are formatted properly and queried with the nvdlib at the NIST CVE API. The found CVEs are processed and outputted.
Challenges
- The used API has a limited number of requests.
- Not all devices have “proper” CPEs.
- It is difficult to automatically determine if the found CVEs are fixed in the next patch.